| .github | ||
| auth | ||
| compose | ||
| config | ||
| controllers | ||
| database | ||
| docker | ||
| docs | ||
| functions | ||
| grpc | ||
| kube | ||
| logger | ||
| logic | ||
| models | ||
| mq | ||
| netclient | ||
| nginx | ||
| scripts | ||
| servercfg | ||
| serverctl | ||
| test | ||
| validation | ||
| .dockerignore | ||
| .gitignore | ||
| CONTRIBUTING.md | ||
| Dockerfile | ||
| go.mod | ||
| go.sum | ||
| LICENSE.txt | ||
| main | ||
| main.go | ||
| mesh-diagram.png | ||
| netmaker.png | ||
| README.md | ||

Create and control automated virtual networks.
WireGuard® Automation from Homelab to Enterprise
- Peer-to-Peer Mesh Networks
- Kubernetes and Multi-Cloud Enablement
- Remote Site Access via Gateway
- OAuth and Private DNS Features
- Support for Linux, Mac, Windows, FreeBSD, iPhone, and Android
Get Started in 5 Minutes
For DigitalOcean, use the 1-Click App:
For production-grade installations, visit the Install Docs.
For an HA install using helm on k8s, visit the Helm Repo.
- Get a cloud VM with Ubuntu 20.04 and a public IP.
- Open ports 443, 80, 53, and 51821-51830/udp on the VM firewall and in cloud security settings.
- Run the script (see below for optional configurations):
wget -qO - https://raw.githubusercontent.com/gravitl/netmaker/master/scripts/nm-quick.sh | sudo bash
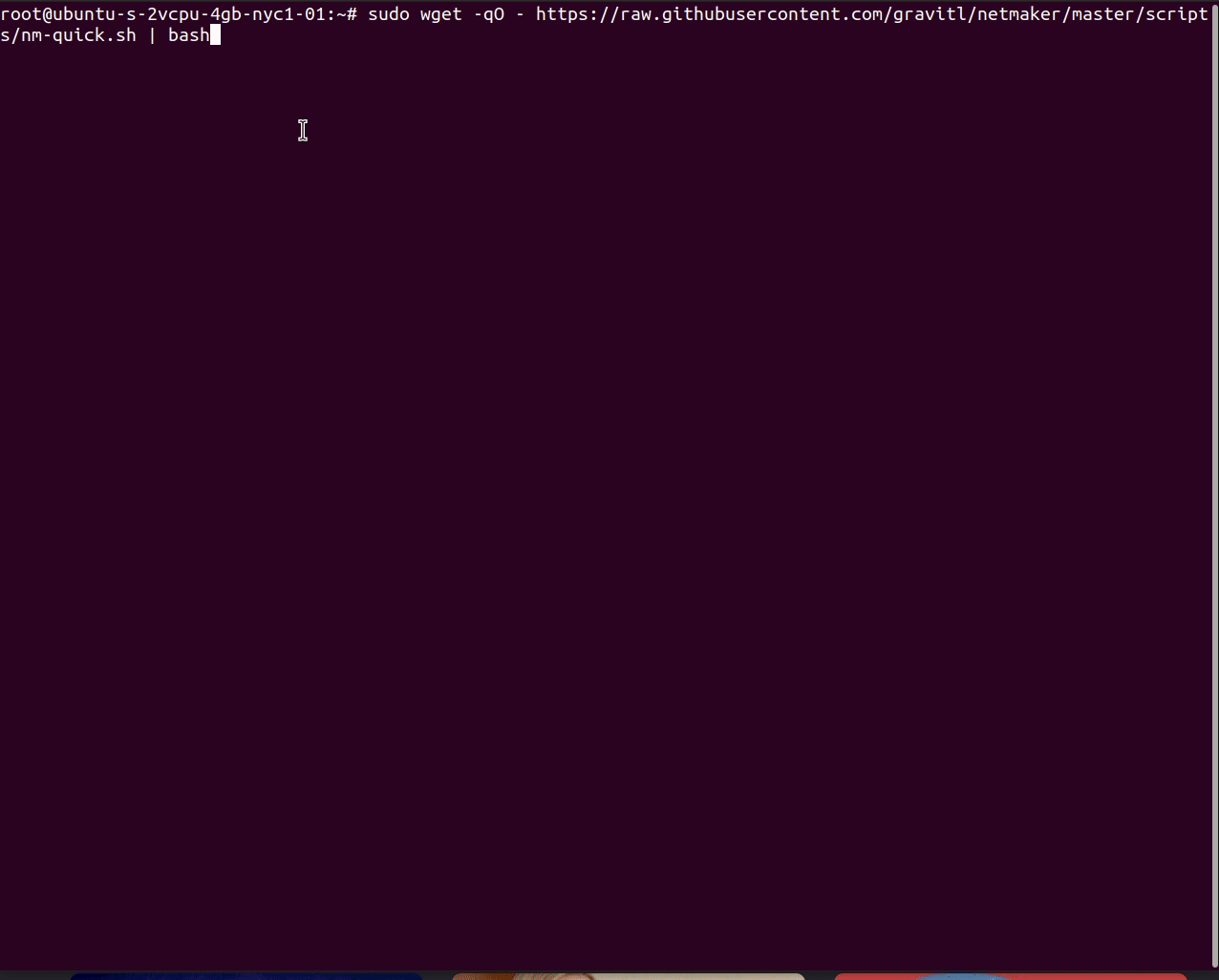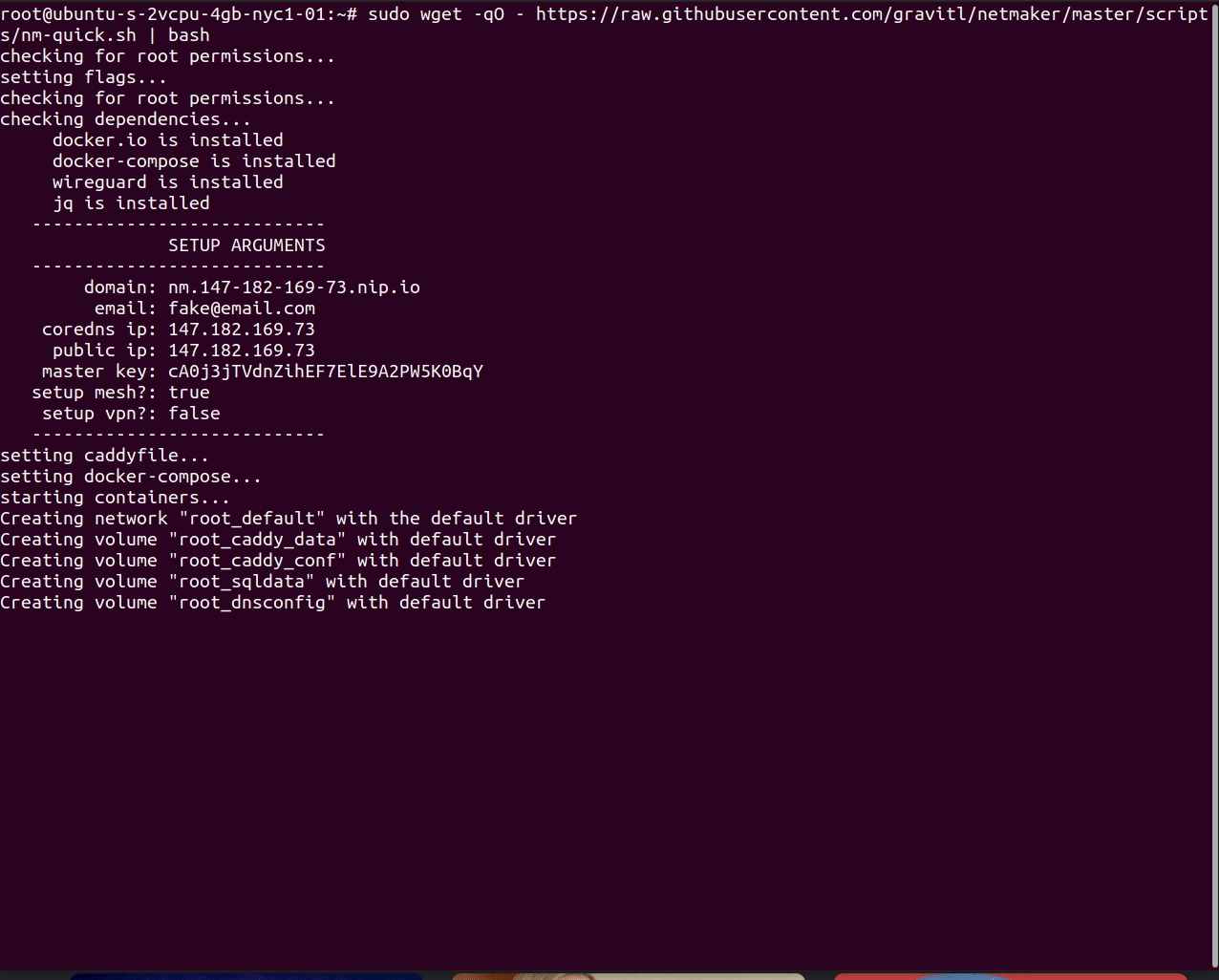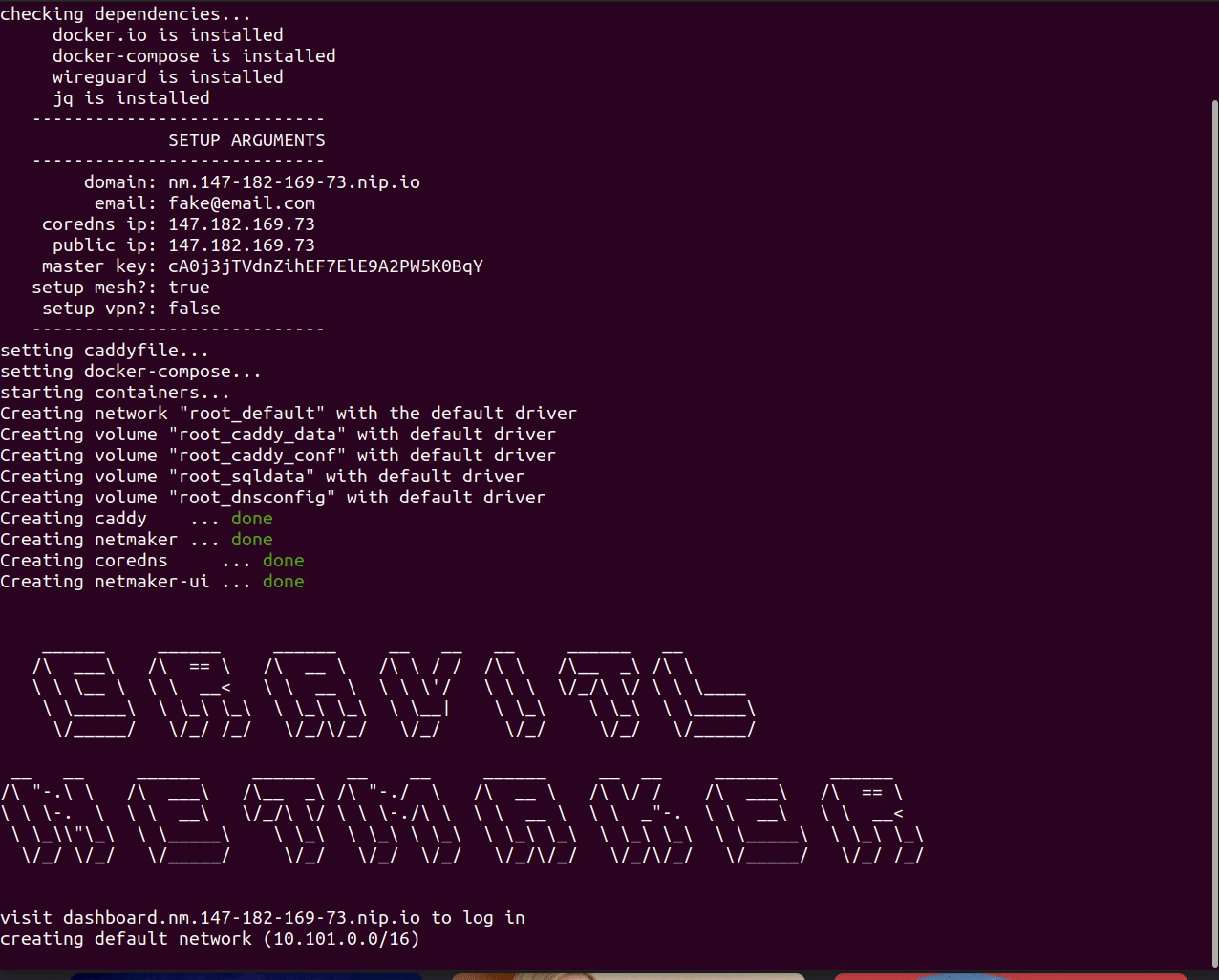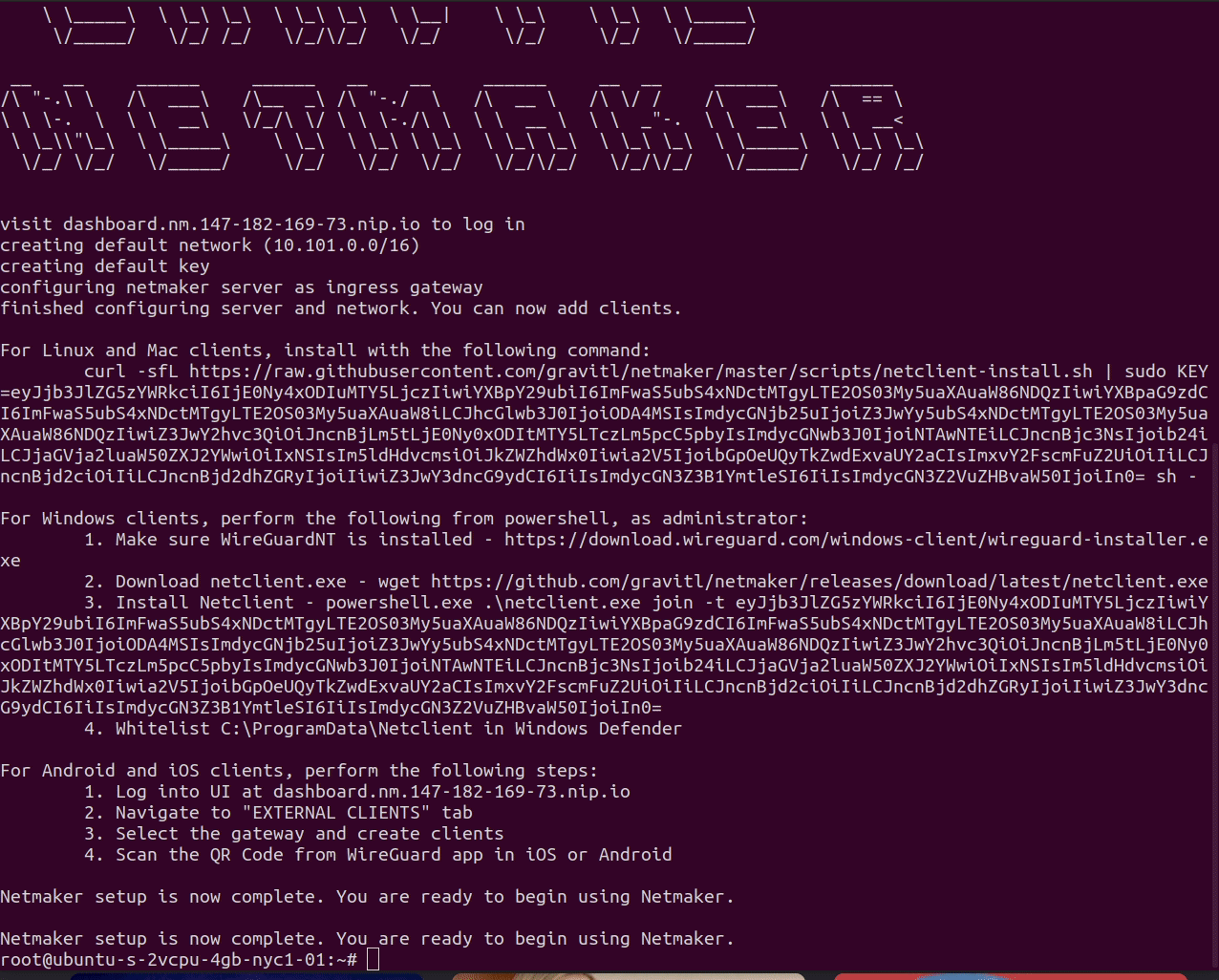

Upon completion, the logs will display the instructions to connect various devices. These can also be retrieved from the UI under "Access Keys."
After installing Netmaker, check out the Walkthrough and Getting Started guides to learn more about configuring networks. Or, check out some of our other Tutorials for different use cases, including Kubernetes.
Optional configurations
Deploy a "Hub-And-Spoke VPN" on the server
This will configure a standard VPN (non-meshed) for private internet access, with 10 clients (-c).
wget -qO - https://raw.githubusercontent.com/gravitl/netmaker/master/scripts/nm-quick.sh | sudo bash -s -- -v true -c 10
Specify Domain and Email
Make sure your wildcard domain is pointing towards the server ip.
wget -qO - https://raw.githubusercontent.com/gravitl/netmaker/master/scripts/nm-quick.sh | sudo bash -s -- -d mynetmaker.domain.com -e example@email.com
Script Options
./nm-quick
-d domain.example.com # specify a wildcard domain for netmaker to use (DNS must point to this server)
-e myemail@example.com # specify your email (for SSL certificates)
-m true # create a default 'mesh network' (on by default)
-v false # create a default 'VPN network' (off by default)
-c 7 # number of client configs to create (for VPN network, 5 by default)
Why Netmaker + WireGuard?
-
Netmaker automates virtual networks between data centers, clouds, and edge devices, so you don't have to.
-
Kernel WireGuard offers maximum speed, performance, and security.
-
Netmaker is built to scale from the small business to the enterprise.
-
Netmaker with WireGuard can be highly customized for peer-to-peer, site-to-site, Kubernetes, and more.
Get Support
Community Projects
Disclaimer
WireGuard is a registered trademark of Jason A. Donenfeld.
License
Netmaker's source code and all artifacts in this repository are freely available. All versions are published under the Server Side Public License (SSPL), version 1, which can be found here: LICENSE.txt.




